Aquia cATO+
What you know of continuous authority to operate (cATO) — plus some
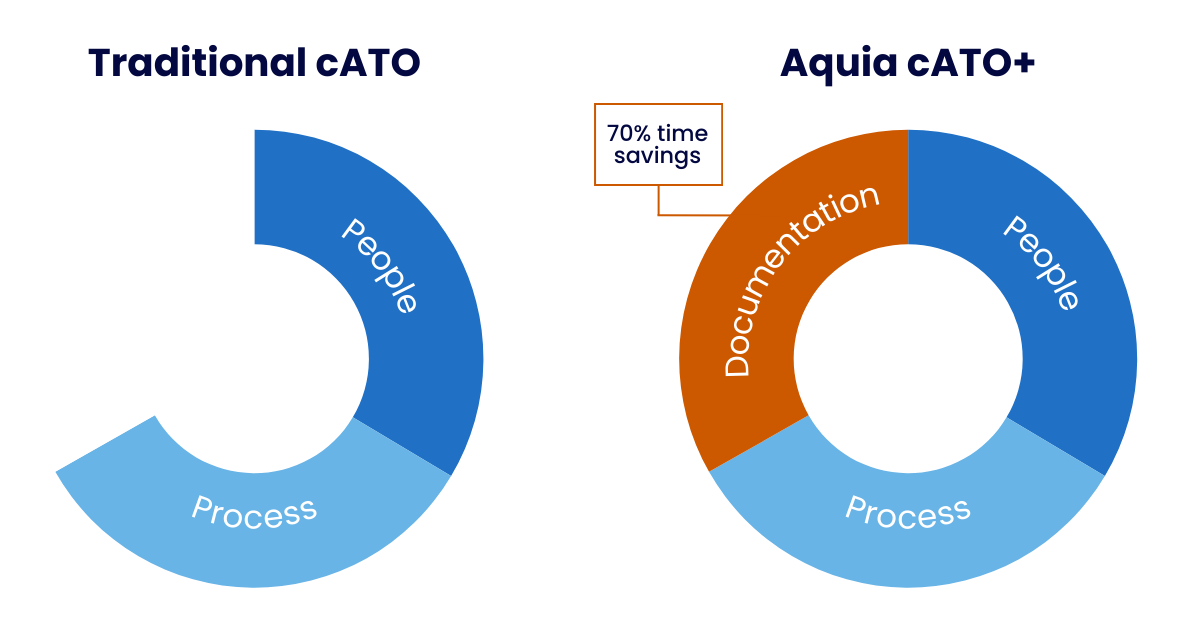
Across the DoD and FedCiv, there is a need to move at the speed of mission while ensuring systems comply with NIST and FISMA requirements. While standard cATO implementations have improved upon traditional ATO processes, they often fall short in addressing the significant documentation burden that creates impediments to modern system development.
Aquia cATO+ addresses this challenge by adding crucial, customized documentation automation.
-
Custom, vetted automations for OSCAL-based system security plan generation reduces SSP creation from weeks to seconds.
-
Pre-vetted implementation statements accelerate compliance documentation with over 70% of implementation statements ready to go.
-
Manual assessment processes are transformed into automated verification procedures.
-
Compliance artifacts are systematically reused across systems and environments.
Security that’s baked in vs. bolted on — empowering developers to focus on active risk reduction vs. documentation exercises.
Aquia cATO+ leverages custom workflows that establish automated security checks and real-time security impact analysis of development changes. We also integrate tools for static and dynamic code analysis, dependency checking, SBOM management, and container scanning to ensure continuous compliance and rapid vulnerability detection across our customers' environments.
Aquia cATO+ leverages:
Infrastructure as code
CI/CD pipelines
Configuration as code
Automated security gates
Continuous monitoring
Automated assessments
Free Resource
Download a copy of our white paper, “cATO+ and Federal Compliance Modernization: Accelerating Continuous Authority to Operate Through Compliance Documentation Automation.”
Not sure where to start?
Aquia cATO Bridge, our native Amazon Web Services (AWS) solution, enables you to begin your cATO journey today. By maximizing CSP-native services already approved in your environment (for example, Audit Manager, Config, Security Hub), we build a clear path to governance, risk, and compliance (GRC) integration.
Benefits of Aquia cATO Bridge:
Immediate visibility into systems
Automated evidence and reporting to jumpstart your cATO readiness
Leadership oversight via dashboards that track posture and trends across many systems
Scalable path to eventually integrate with a dedicated GRC tool for all systems
Request a Consultation
We’re in good company.
Work With Us
GSA Schedule and SINS
GSA Schedule 47QTCA23D000H
SIN 518210C Cloud Computing and Cloud
SIN 54151HACS Highly Adaptive Cybersecurity Services (HACS)
SIN 54151S Information Technology Professional Services
Federal Contract Vehicles
USDA STRATUS Cloud BOA
VA SPRUCE IDIQ
Company Profile
CAGE Code: 8XPQ4
DUNS: 117948867
Unique Entity ID: RGMQQK1DLAN9
NAICS Codes
541511 Custom Computer Programming Services (primary)
334111 Electronic Computer Manufacturing
334112 Computer Storage Device Manufacturing
334310 Audio And Video Equipment Manufacturing
334419 Other Electronic Component Manufacturing
518210 Data Processing, Hosting, And Related Services
519130 Internet Publishing And Broadcasting And Web Search Portals
519190 All Other Information Services
541430 Graphic Design Services
541512 Computer Systems Design Services
541513 Computer Facilities Management Services
541519 Other Computer Related Services
541611 Administrative Management And General Management Consulting Services
541614 Process, Physical Distribution, And Logistics Consulting Services
541618 Other Management Consulting Services
541715 Research And Development In The Physical, Engineering, And Life Sciences (Except Nanotechnology And Biotechnology)
561110 Office Administrative Services
561320 Temporary Help Services
561439 Other Business Service Centers (Including Copy Shops)
611420 Computer Training
Partnerships
AWS Advanced Tier Services Partner
AWS Public Sector Partner
AWS Global Security and Compliance Acceleration program (ATO on AWS)
AWS Security Partner
GCP Partner
Membership
Digital Services Coalition
National Veteran Small Business Coalition (NVSBC)

Stay in the Know
Sign up to receive updates.